Configuring Microsoft Active Directory
Iron Speed Designer and your application should run on any computer which is in your Active Directory and has proper access to Active Directory. Proper access means both that (a) you can log into your computer using the domain user name and also (b) Iron Speed Designer and your application can retrieve information from the Active Directory such as the root path, search the Active Directory and perform other standard operations.
Configuring Microsoft IIS to work with Active Directory
In the ‘Directory Security, Anonymous access and authentication control’ section of the Microsoft IIS Properties menu:
-
Set IIS Authentication Methods to ‘Integrated Windows Authentication’
-
Disable ‘Anonymous access’
To allow Single Sign-In (application uses credentials of currently signed in user from Active Directory) on a deployed application, set:
Impersonate = “false”
Note, on localhost these settings will do the opposite: they will effectively disable Single Sign-In and also will disable Windows authentication for your database, so these settings should be done on deployed (production) applications only.
Important information for users of Iron Speed Designer V5.2 and earlier: In Version 6.0 and later releases, single sign-in functionality requires the above settings to operate properly and avoid signing in twice. You will need to update your Microsoft IIS settings when using Iron Speed Designer V6.0 and later.
Configuring Microsoft Internet Explorer to work with Active Directory
To allow user authentication, Microsoft Internet Explorer must pass the user’s credentials to your application. Information on how to configure Microsoft Internet Explorer can be found in:
http://www.microsoft.com/windows/ie/ie6/using/howto/security/setup.mspx
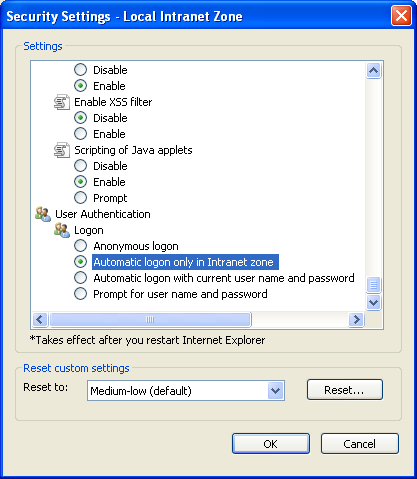
In Microsoft Internet Explorer, the User Authentication option controls how HTTP user authentication is handled. Enable the ‘Automatic login with current user name and password’ option. This eliminates unnecessary (duplicate) sign in prompts.
Verifying your Active Directory connection
Check if other Active Directory utilities such as Administrative Tools, Active Directory Users and Computers; and Administrative Tools, Active Directory Sites and Services can start. If they can’t find the domain or connect to the domain controller, most likely:
-
Your computer is not in the Active Directory
-
Your Active Directory is improperly configured, or
-
You computer is improperly configured
Contact your IT administrator to properly configure your Active Directory.
Configuring your Machine.config file
The processModel property in machine.config file should be either:
-
<processModel autoConfig="true" />
This is the default configuration. In this case, Microsoft IIS assigns any process to the ASPNET built-in user with a low permission level. Your application will not be able to access the AzMan policy store located in the Active Directory. -
<processModel enable="true" userName="username" password="userpassword" />
Microsoft IIS assigns a process identity to userName.
Note: If you assign processModel to the built-in System account, most likely the Microsoft Authorization Manager (AzMan) API will not work.
The machine.config file is located in:
C:\<windows>\Microsoft.NET\Framework\<version>\config\machine.config
View State configuration and Active Directory
Sometimes your application server and Active Directory configurations can affect the behavior of Active Directory Security in Iron Speed Designer applications. If application users experience sporadic problems logging in after a period of inactivity then try changing your application’s View State setting to “Session” instead of “Page” (Build, Performance Tuning...).